Follow the steps to use free internet in airtel :-
- First Download vpn from your-freedom.net
- Register your account
- Make sure you remember your user name and password that you must use to login into vpn.
- Now open the downloaded vpn
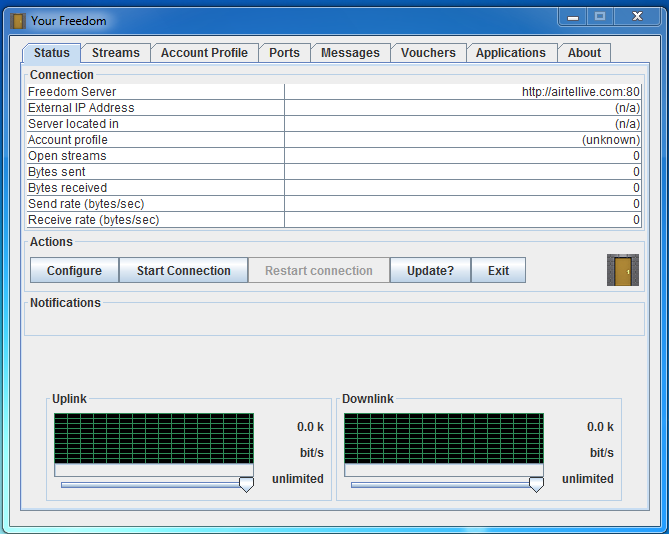
- Select Configuration under action
- Enter as given in the above picture (server connection)
- In proxy settings enter as mentioned in above diagram.
- Go to Account Information and enter your username and password.
- Now click Save and exit
- Now open Your Freedom vpn, select port option and enter as mentioned in the image given below.
- Now go to your browser(chrome or firefox ) .Go to proxy settings and enter the proxy as 127.0.0.1 and enter the port as 1234.
- Now connect your airtel modem (normal connection).
- Go to status in vpn and select Start Connection.
- Now you can access free internet.